Ctrl + F is the shortcut in your browser or operating system that allows you to find words or questions quickly.
Ctrl + Tab to move to the next tab to the right and Ctrl + Shift + Tab to move to the next tab to the left.
On a phone or tablet, tap the menu icon in the upper-right corner of the window; Select "Find in Page" to search a question.
Share UsSharing is Caring
It's the biggest motivation to help us to make the site better by sharing this to your friends or classmates.
Computer Numerical Control
A comprehensive guide to understanding and operating CNC machines, covering programming, machining techniques, and applications in manufacturing and automation.
cnc
machining
automation
precision
programming
manufacturing
cutting
milling
turning
drilling
cad/cam
tooling
workpiece
accuracy
efficiency
robotics
It is a connectionless protocol, which means that it sends the data without checking whether the system is ready to receive or not.
- TCP
- UDP
- HTTP
- HTML
With the advantage of easier programmingprovided by the OS, the hardware, its machinelanguage and the OS constitutes a new combinationcalled as a _____________________
- virtual (extended) box.
- virtual (peripheral) machine.
- virtual (extended) machine.
- virtual (extended) ware
It is to provide the communication services directly to the application processes running on different hosts.
- Transport Layer
This device was invented back in 2400 B.C in Babylonia.
- Napier's Bone
- Abacus
- Ishango Bone
- Stepped Reckoner
who invented the Atanasoff-Berry Computer?

- Prof John Atanasoff
The transport layer transmits the entire message to the destination.
- End-to-end delivery
- Addressing
- Reliable delivery
- Flow control
A programmable machine that manipulates data according to instructions.
- Calculator
- Computer
- Mobile Phone
- Laptop
Radius gauge is made of
- High quality steel sheet
- HSS
- HCS
- LEAD
is a directory service that provides a mapping between the name of a host on the network and its numerical address.
- Domain Name System
Who is in this Photo?Hint: His creation was inspired by Charles Babbage's difference engine.

- Herman Hollerith
- John Presper Eckert
- Per Georg Scheutz
- Von Neumman
Match the advantage of below input device
- Can be used by disabled people who may not have freedom of movement
- Trackerballs
- Fast method of input
- Mouse
- Allows user to control movement far more accurately than a mouse
- Driving Wheel
- Hard-copy material can be changed into digital form
- Scanners
- Readings are more accurate than humans
- Sensor
Involve the execution of various tasks such ascreation of processes, scheduling of processes,management of deadlock, and termination ofprocesses.
- PROCESSMANAGEMENT
_________________ is the functionality of anthe operating system which handles or managesprimary memory and moves process back andforth between main memory and disk duringexecution.
- Memory management
Axis for depth cut
- Y
- Z
- X
- W
Hardware devices that allow data to be transmitted to a computer is called?
- Output Devices
- Input Devices
- Direct Data Entry
- Storage Devices
According to the layered model, the transport layer interacts with the functions of the session layer.
- End-to-end delivery
- Addressing
- Reliable delivery
- Multiplexing
OS uses the _____________ of the microprocessor,whereas other programs use the____________.
- safe mode
- kernel mode
- user mode
What is Numerical Data (NC) in CNC Milling machine?
- G Code M Code
The distance between tip to the heel of file
- File length
- heel
- Tip
- Ferrule
The father of all machine is
- Lathe
- Drilling
- Milling
- Grinding
Tree Popular Operating Systems
- Linux
- Linux
- Symbian
- Windows
- Mac
The computer which uses FTP to transfer data is called the.......
- FTP server
The closest layer to the end user which means that the application layer and end user can interact directly with the software application. The application layer programs are based on client and servers.
- Application Layer
- Network Virtual terminal
- Addressing
- Mail Services
The UDP stands for?
- User Datagram Protocol
The Jacquard Loom was invented by _______ in the year 1881.
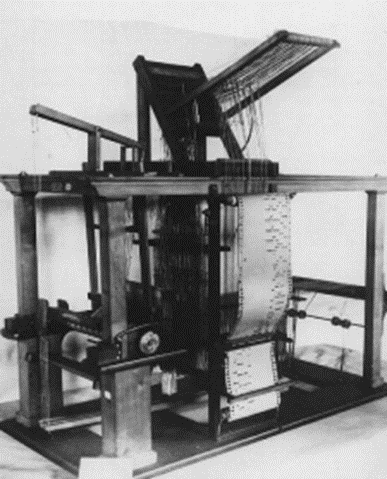
- Josie-Mary Jacquard
- Joseph-Marie Jacquard
- John-Marie Jacquard
- Josey-Marie Jacquard
It is used to prevent the sender from overwhelming the receiver. If the receiver is overloaded with too much data, then the receiver discards the packets and asking for the retransmission of packets.
- End-to-end delivery
- Addressing
- Reliable delivery
- Flow control
in what year did Thomas de Colmar invented the Arithmometer ?
- 1920
- 1832
- 1820
- 1822
A ... is an output device that is used to display an image of what your computer is doing.
- monitor
Match the following
- Able to input data from a hard-copy documents which is much quicker than retyping them
- OCR
- Allows user to swipe, use one, two of more fingers for different functions
- Touchpad
- Small, handheld device that can be used to operate equipment such as Tv and AC
- Remote control
- Can be use to scan a sheet of paper and identify any marks on it
- OMR
Hacksaw blade is made of
- HCS
- HSS
- CARBIDE
- NONE
Another aspect for theusage of OS is that; it isused as a _________________for hardware-softwareinteraction.
- predefined application
- predefined interface
- predefined library
- predefined software
a program that runs on the local machine requesting service from the server.
- Client
State the basic axis in CNC Milling machine.
- V,W,X
- U,Y,Z
- X,Y,Z
- U,V,W
Which is not CNC Milling machined part or product
- Image: https://quizizz.com/media/resource/gs/quizizz-media/quizzes/b5014dbc-c811-47df-b66c-9c2c50a82e20?w=90&h=90
- Image: https://quizizz.com/media/resource/gs/quizizz-media/quizzes/75487710-4cf2-4e9e-8890-5d7a5006c21c?w=90&h=90
- Image: https://quizizz.com/media/resource/gs/quizizz-media/quizzes/a293429f-5363-4deb-b087-d0866b8c098b?w=90&h=90
- Image: https://quizizz.com/media/resource/gs/quizizz-media/quizzes/9b023e49-db7b-4eaf-a2e7-08c739c625b3?w=90&h=90
is a physical or virtual internetworking device that is designed to receive, analyze, and forward data packets between computer networks
- Router
Who invented the Tabulating Machine?
- Howard Aiken
- Professor John Atanasoff
- John Mauchly
- Herman Hollerith
Essay: What is the importance of computer in our daily life?What do you think are the pros and cons of the development of computers?
- [No Answer]
Types of sensor that is used in washing machine, central heating systems, and ovens
- Moisture
- Pressure
- Light
- Temperature
Which of the 7 Characteristics of computer can perform millions of tasks or calculations with the same consistency and accuracy.
- Speed
- Versatility
- Diligence
- Accuracy
Which of these is a disadvantage of using CAD over hand drawing designs?
- You can easily share the file to anyone in the world via email.
- You can make multiple changes to the design without having to re-draw it.
- CAD programs are expensive and hard to learn.
- You can manufacture multiple copies of your design very easily.
The technique which is used to validate the authenticity and integrity of the message.
- Digital Signature
Which one of these images is NOT an example of CAM?
- Image: https://quizizz.com/media/resource/gs/quizizz-media/quizzes/589ed30d-9b6e-4cbc-9799-ad7ff6b5e8ae?w=90&h=90
- Image: https://quizizz.com/media/resource/gs/quizizz-media/quizzes/6c6e01cb-4e17-40ff-ba36-dd975099f680?w=90&h=90
- Image: https://quizizz.com/media/resource/gs/quizizz-media/quizzes/a8c57826-3be3-4529-9be7-d659cab2d9de?w=90&h=90
- Image: https://quizizz.com/media/resource/gs/quizizz-media/quizzes/fe2ccc69-682e-4c71-a639-45e8e38fde94?w=90&h=90
Blaise Pascal invented the _______ in 1642.
- Pascaline
Fixed and provides a set of services to applications.
- Network architecture
- Architecture
- Client-server
- P2P (peer-to-peer) architecture:
program that runs on the remote machine providing services to the clients.
- Server
CAM stands for:
- Computer Aided Manufacture
- Computers and Making
- Computer Aided Making
- Computers and Manufacturing
In general, a computer system has some resourceswhich may be utilized to solve a problem. Which is NOT belong.
- Memory
- Processors
- I/O
- File System
- Disk Scheduling
Choose two advantages of video camera compared to digital camera
- Record audio as well as images
- Record audio as well as images
- Easier and faster to upload images
- Easier to manipulate footage using specialist software
It is an advantages of Client-server networks as the use of the dedicated server increases the speed of sharing resources
- Centralized
- Security
- Performance
- Scalability
A set of instruction to be executed
- PROCESSCODE
DDE device that function as security device to allow entry to buildings, hotel rooms. called?
- Contactless card reader
- Chip & PIN reader
- Magnetic stripe reader
- OMR
The least count of vernier calliper
- 0.2mm
- 0.02mm
- 0.01mm
- 0.002mm
The point angle of drill bit
- 1180
- 900
- 450
- 600
Havard Mark 1 was invented by Howard H. Aiken in the year ____.
- 1936
- 1953
- 1943
- 1940
What did you enjoy about this project?
- [No Answer]
The First Generation Computer uses ______ for circuitry and magnetic drums for memory and were often enormous, taking up entire rooms.
- vacuum tubes
Full form of CNC
- Computer numerical Control
How do you think this project could be improved?
- [No Answer]
Input device that is used to input their PIN numbers when they pay for something by card, called?
- Mouse
- Keyboard
- Numeric keypads
- Touch screen
implies the management of the I/O devices such asa keyboard, magnetic tape, disk, printer,microphone, USB ports, scanner, camcorder etc.aswell as the supporting units like control channels.
- DEVICEMANAGEMENT
It is a connection-oriented protocol, which means that the connection needs to be established before the data is transmitted over the network.
- TCP
- UDP
- HTTP
- HTML
Describe the image operation
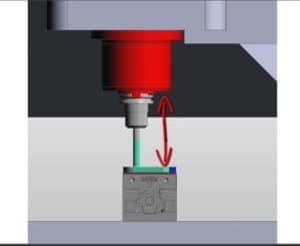
- Programming
- Tool selection
- Datum point
- Tool length offset
CAM stands for Computer Aided ___________
- manufacture
What does ENIAC stand for?
- Electronic Numerical Integrator and Calculation
- Electronic Numerical Integral Computer
- Electrical Number Integrator and Computer
- Electronic Numerical Integrator and Computer
What DDE device that has key feature that able to track livestocks?
- Barcode reader
- RFID
- MICR
- OCR
is an interface that defines how data and commands are sent across the network.
- network virtual terminal
- TELNET
- Remote login
- Local Login
This DDE device has a disadvantage of special designed forms in order for the reader to read it accurately
- OMR
- OCR
- MICR
An OS provides services for (SELECT ALL POSSIBLE ANSWERS)
- Processor Management
- Processor Management
- Memory Management
- Disk Management
- File Management
- Concurrency Control
simple protocol and it provides nonsequenced transport functionality.
- User Datagram Protocol
The very first computer programmer which helps program the Analytical Engine
- Ada Wong
- Ada Byron Ace
- Ada Bryon Lovace
- Ada Lovelace
The Very First Portable Computer
- UNIVAC 1
- ENIAC
- Osborn 1
- Havard Mark 1
consists of measures taken by business or some organizations to monitor and prevent unauthorized access from the outside attackers.
- Computer Network Security
What is CNC word stands for?
- Computer Numerical Control
CAD stands for Computer _____ Design
- aided
__________ invented the very first programmable computer in Germany from 1936 to 1938.
- Konrad Zuse
The invention that replaced the Vacuum tubes. This invention was faster and more efficient to use than the Vacuum Tubes.
- Integrated Circuit
- Transistors
- CPU
- Sillicon Chips
A types of connections in FTP: uses very simple rules for communication
- Control Connection
What is MICR stands for?
- Magnetic Ink Character Recognition
- Mark Ink Character Recognition
- Magnetic Infuser Character Recognition
- Magnetic Ink Compiler Recognition
Gottfried WIlhelm invented the ________ in 1672
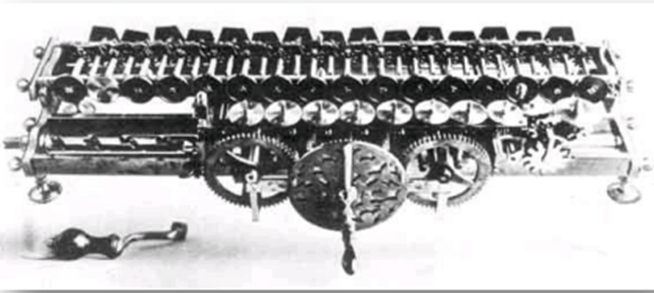
- Stepping Calculator
- Abacus
- Stepped Reckoner
- Atanasoff-Berry Computer
For high volume printing inkjet printer are considerably cheaper to run
- TRUE
- FALSE
Manages all types of data and files in an operatingsystem (OS), or a database management system(DBMS), which has a relational databasecapabilities and includes a programming languagefor further data manipulation.
- FILEMANAGEMENT
This computer characteristic "refers to the capability of a computer to perform different kind of work in the same accuracy and efficiency."
- versatility
Input device that only works with CRT monitors called?
- Graphics tablet
- Stylus
- Light pens
- Touch screen
The important angle for chipping
- Clearance angle
- Rake angle
- Point angle
Which tool in 2D Design allows you to delete parts of your drawing?
- Image: https://quizizz.com/media/resource/gs/quizizz-media/quizzes/e9609967-9e86-4a82-949d-db20c4a21e9c?w=90&h=90
- Image: https://quizizz.com/media/resource/gs/quizizz-media/quizzes/20c572c1-ec16-45a7-8a4b-f4dd0c925880?w=90&h=90
- Image: https://quizizz.com/media/resource/gs/quizizz-media/quizzes/5795d8d0-3d47-4882-91d5-a70ad2f15a21?w=90&h=90
- Image: https://quizizz.com/media/resource/gs/quizizz-media/quizzes/9d6ad873-7510-4b1d-abac-b0f6a148cffd?w=90&h=90
Out of these input devices, which one has the disadvantages of the display may get dirty, then become less-visible and cause malfunction.
- Joystick
- Touch screen
- Keyboard
- Pointing device
List FOUR (4) CNC Milling Tools
- End Mill
- End Mill
- Boring
- Face Mill
- Dovetail
- Ball Mill
It is an advantages of Client-server networks as these networks are more secure as all the shared resources are centrally administered.
- Centralized
- Security
- Performance
- Scalability
Which is the 2D Design tool which lets you draw lines?
- Image: https://quizizz.com/media/resource/gs/quizizz-media/quizzes/658f2176-a8b1-4279-a6e6-b5068da0b379?w=90&h=90
- Image: https://quizizz.com/media/resource/gs/quizizz-media/quizzes/04d2164a-32e3-419e-bccd-8b5e6a1fb0c7?w=90&h=90
- Image: https://quizizz.com/media/resource/gs/quizizz-media/quizzes/302f2cff-00ce-462f-a672-ce24d5db1d51?w=90&h=90
- Image: https://quizizz.com/media/resource/gs/quizizz-media/quizzes/972f2129-2b81-45e8-90a2-8c9c98927df4?w=90&h=90
The TCP stands for?
- Transmission Control Protocol
Resources that a process required forits execution
- PROCESSCOMPONENTS
Invented by Gottfried Wilhelm Leibniz in 1672
- Jacquard Loom
- Aritmometer
- Stepped Reckoner
- Pascaline
Which one of these images is NOT an example of CAD?
- Image: https://quizizz.com/media/resource/gs/quizizz-media/quizzes/a3eb84d5-1b3a-402d-a97e-24f0cb6ddc92?w=90&h=90
- Image: https://quizizz.com/media/resource/gs/quizizz-media/quizzes/e01a30bf-4459-46f8-a5b0-5b40703c3f4b?w=90&h=90
- Image: https://quizizz.com/media/resource/gs/quizizz-media/quizzes/5ac3c5d7-51be-4fc8-bfb7-8f29ceda1cef?w=90&h=90
Aspects of Network Security: means that the receiver must be able to prove that the received message has come from a specific sender.
- Privacy
- Message Integrity
- End-point authentication
- Non-Repudiation
Aspects of Network Security: means both the sender and the receiver expects confidentiality. The transmitted message should be sent only to the intended receiver while the message should be opaque for other users.
- Privacy
- Message Integrity
- End-point authentication
- Non-Repudiation
ENIAC stands for
- Electronic Numerical Integrator andComputer
What device is in this Photo?

- Abacus
- Tally Stick
- Scheutzian Calculation Engine
- Napier's Bones
CAD stands for:
- Computer and Design
- Computer Aided Design
- Computer Added Design
- Computing and Designs
What does CNC stand for?
- Computers and Control
- Computers and Carpentry
- Computer Numerical Control
- Controlled Numerically Computers
Aspects of Network Security: means that the receiver is sure of the sender?s identity, i.e., no imposter has sent the message.
- Privacy
- Message Integrity
- End-point authentication
- Non-Repudiation
File is made of
- HCS
- HSS
- HFS
- NONE
This output device can be totally portable , but has a disadvantage of relying on a powerful and expensive bulb to provide the pictures on a big screen
- Laser Printer
- Multimedia projector
- 3D printers
- Plotter
The transport layer provides reliability services by retransmitting the lost and damaged packets.
- End-to-end delivery
- Addressing
- Reliable delivery
- Multiplexing
An OS is a program that acts as an ______________between computer system users and the computerhardware.
- Gui
- Design
- Interface
- None of the Above
It is a big problem in Client/Server networks. When a large number of clients send requests to the same server may cause the problem.
- Traffic Congestion
A types of connections in FTP: uses very complex rules as data types may vary.
- Data Connection
Advantage of CNC Milling machine
- expensive
- consistent
- accurate
- non skill operator
- safe
..... are devices that read data from a source that's provided and transferred it directly to the computer system
- DDE
A device that inputs data to a computer. The data is a measurement of some physical quantity that is continuously changing.
- Microphones
- Digital Camera
- Sensors
- Graphic tablet
An operating system is a program that acts as an interface between the user and the computer hardware and controls the execution of all kinds ofprograms.
- True
- False
Identify this picture what type of log in is this.

- Local Login
- Remote login
Your jigsaw was made from MDF, what does MDF stand for?
- Medium Density Fibreboard
- Middle Density Fibreboard
- Low Density Fibreboard
- Medium Depth Fibreboard
CNC stands for: Computer Numerical ______
- Control
List THREE (3) CNC Milling machine components
- Work holding Device
- Work holding Device
- Machine tool
- Compressor
- Spindle
Which tool in 2D Design allows you to convert an image to laser cut?
- Image: https://quizizz.com/media/resource/gs/quizizz-media/quizzes/4dd00ad3-2b16-414a-94ae-6e7f1c6407cd?w=90&h=90
- Image: https://quizizz.com/media/resource/gs/quizizz-media/quizzes/366bea7d-f449-40f0-885d-65e0256206c7?w=90&h=90
- Image: https://quizizz.com/media/resource/gs/quizizz-media/quizzes/61c3e237-4612-407a-881f-bc91023977da?w=90&h=90
- Image: https://quizizz.com/media/resource/gs/quizizz-media/quizzes/45e36612-acfd-4c1a-bfc7-b628ec5887cb?w=90&h=90
Define Milling machine revolution era
- Digital Display
- Digital Display
- Coolant
- Programming
- Virtual technology
QR code is made up of a matrix of filled in dark squares on a light background. What is QR stands for?
- Quick Role
- Quick Response
- Quick Runtime
- Quick Registry
____ is a device that moves or controls some mechanism
- Sensor
- Actuator
- Dynamo
- Buzzer
It is an advantages of Client-server networks as back-up is possible in client-server networks, i.e., all the data is stored in a server.
- Centralized
- Security
- Performance
- Scalability
A standard internet protocol provided by TCP/IP used for transmitting the files from one host to another.
- File transfer protocol
The transport layer uses the multiplexing to improve transmission efficiency.
- End-to-end delivery
- Addressing
- Reliable delivery
- Multiplexing
_____ are used for everything that requires a text or numerical input, from writing an email to writing a book.
- Keyboard
Aspects of Network Security: means that the data must arrive at the receiver exactly as it was sent.
- Privacy
- Message Integrity
- End-point authentication
- Non-Repudiation
Lathe bed is made of
- Grey Cat Iron
- Steel
- Plastic
- Carbide Material
Identify this picture what type of log in is this.

- Local Login
- Remote login
It is an advantages of Client-server networks as we can increase the number of clients and servers separately, i.e., the new element can be added, or we can add a new node in a network at any time.
- Centralized
- Security
- Performance
- Scalability
To keep up this site, we need your assistance. A little gift will help us alot.
Donate- The more you give the more you receive.
Related SubjectManufacturing Technology
Quality Assurance Testing
Configuration Management
Software Development
Mechatronics
Industrial Electronics Maintenance
Engineering
Computer-Aided Design
Programmable Logic Controller
Unified Functional Testing
Computer Aided Drawing
Application Development and Emerging Technology
BMW M3 Performance and Engineering
Quantum Computers
Programming vs Coding
Origin of Women in Computing
Computer Information Systems
Computer Science
Introduction to Computing
Introduction to Multimedia
Database Management System
Data Structures and Algorithms
Computer Fundamentals
3D Game Art Development
Boeing: A Century of Aerospace Excellence
Electronics Engineering Technology
Apparel Construction
Driving Test
Additive Manufacturing
Bookkeeper and Clerk
Data Communications and Networking 2
Cybertruck Technology
The Supply Chain
Supersonic Air Travel
Germany Energy Policy
Apple M4 Macs
Office Assistant
Maintenance Technology
Management
Inventory Production Control
Health Care Office Manager
Fast Track
Administrative Assistant
Public Finance
Basic Microeconomics
Algorithms and Complexity
Show All Subject
Affiliate Links
Shopee Cashback Voucher
Temu $0 Shipping Fee
Amazon 75% Off Discounts